
ISO 27001 in an IT Company. What are the Implementation and Its Benefits?
In today's digital world, where data is one of the most valuable resources, protecting information is a priority. Especially for companies that develop dedicated software and have access to sensitive data, taking care of security standards is essential. At Droptica, we already know that implementing ISO 27001 ensures adequate data protection, translating into greater customer trust. Let's take a look at what the process entails and its benefits.
What is ISO 27001?
ISO 27001 (or ISO/IEC 27001) is the international standard for information security management created by the International Organization for Standardization. Its purpose is to establish, maintain and improve an information security management system (ISMS) that ensures the protection of data confidentiality, integrity, and availability within an organization.
Standard ISO 27001 specifies a series of security controls that a company must implement and maintain, covering both technical and organizational aspects. The standard is flexible and can be adapted depending on the organization type, industry, and company size.
ISO 27001 implementation - the flow of process
Implementing a security standard in a company is a complex process that requires the cooperation of many departments and the entire company's involvement. Organizations seeking certification of the ISO 27001 may be subject to a security audit verifying compliance with the principles of the international standard, so it’s vital to prepare accordingly. Let's see what steps are involved in ISO 27001 implementation.
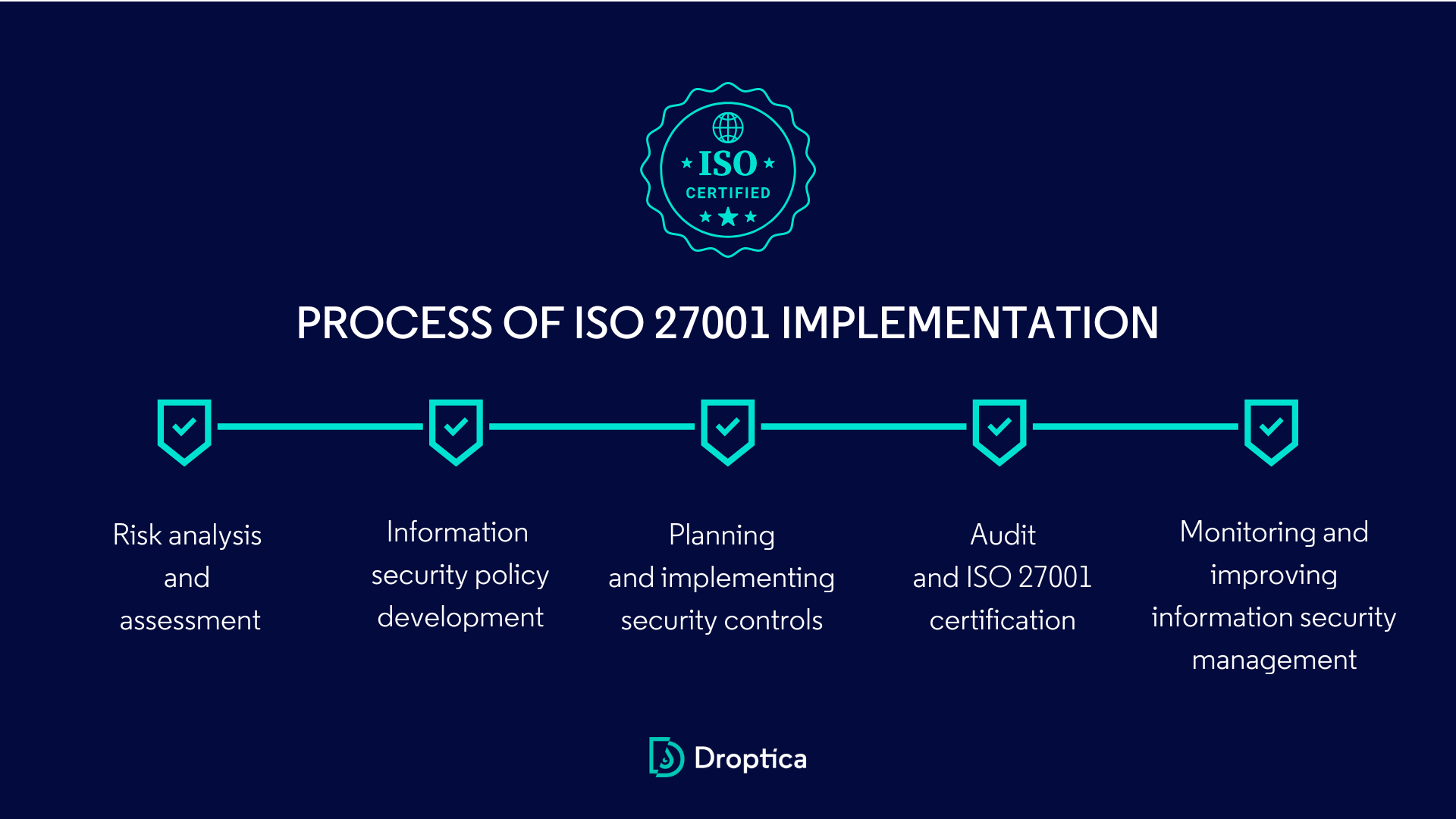
1. Risk analysis and assessment
The first step in implementing ISO 27001 is to conduct a risk analysis and assessment. This involves identifying potential threats to the company's information security and assessing their impact and likelihood of occurrence.
The risk analysis should consider both external threats, such as hacking attacks, data theft, or server crashes, and internal dangers, such as unauthorized employee actions, sharing access to systems with third parties, or leaving company equipment unattended.
2. Information security policy development
Another critical step is developing an information security policy. This document is the basis for effective information security management and creating awareness within the organization about the priority of data protection.
The company's security policy information should consist of such elements as:
- Information security objectives: the document should indicate the goals that the organization aims to achieve regarding information security. These may include, for example, maintaining data confidentiality, ensuring information integrity, minimizing the risk of security breaches, or ensuring business continuity of information systems.
- Rules of conduct: policy should comprise regulations that define the expected employees’ and other stakeholders’ behavior in the context of information security. These can include guidelines for using information systems (e.g., CRMs, intranet systems), password management, information sharing, or risk management.
- Accountabilities: the document should clarify the roles and responsibilities of individuals for implementing, maintaining, and monitoring the information security policy. This helps ensure a clear delineation of duties and define accountability for information protection.
- Guidelines and procedures: policy can also include other guidelines in line with the specifics of the business and refer to detailed information security procedures and documents. This allows for a more precise discussion of specific aspects, such as access management, incidents, or external vendors.
The information security policy should be a document that is easy to understand, accessible to all employees, and regularly updated according to the organization's changing requirements.
3. Planning and implementing security controls
Based on the risk analysis and the strategic policy document, a company should develop an action plan that includes specific steps to enhance information security. This plan should consider both technological and organizational aspects.
The implementation of security controls may include activities such as:
- access control of the company's systems,
- backup preparation,
- network and server monitoring,
- information security training for employees,
- and many others.
4. Audit and ISO 27001 certification
Once security controls have been implemented, the organization should conduct an internal audit to assess the effectiveness of the measures implemented and ISO 27001 compliance. It’s worth using external audit assistance to ensure the process is independent and objective.
If the completed audit confirms compliance with the requirements, the organization can apply for ISO/IEC 27001. Having such a certificate is the official confirmation that the company meets international information security standards.
5. Monitoring and improving information security management
Monitoring the effectiveness of implemented security controls and actions is another crucial step in the process. It includes regular reviews of security indicators (including the number of incidents, response times, and signals of management system performance), audit results evaluation, and analysis of information security situations. This makes it possible to identify areas for improvement.
Based on this information, a corrective action plan can be developed to include patches, procedure updates, employee training, and the implementation of new technologies or tools to enhance information security. It’s also essential to maintain awareness among employees to continually emphasize the importance of data security and encourage reporting of potential threats or incidents.
Benefits of ISO 27001
Implementing ISO 27001 in a dedicated software development company brings numerous advantages, building trust and customer loyalty. Here are some examples of the benefits of ISO 27001 certification:

- Protecting customer data: implementing ISO 27001 standard requires an organization to focus on protecting data confidentiality, integrity, and availability. Through appropriate technological safeguards and procedures, the company minimizes the risk of customer data being breached, stolen, or lost.
- Credibility and client trust: having ISO 27001 certification confirms to customers that the company adheres to high information security standards. This builds credibility and trust in clients' eyes, who are looking for business partners that take proper care to protect their data.
- Meeting regulatory requirements: many sectors, such as finance and healthcare, require the companies they work with to adhere to specific information security standards. Having ISO 27001 certification makes it easier to meet these regulatory requirements, which is essential for customers operating in these sectors.
- Better risk management: by implementing ISO/IEC 2700, the company gains better information security risk management. By conducting a risk analysis and implementing appropriate controls, the company is prepared for potential threats, resulting in greater security of customer data.
ISO/IEC 27001 standard - summary
Implementing ISO 27001 in an IT company is a complicated process, but one that is extremely important for ensuring information security. The course of the process includes, among other things, risk analysis, information security policy development, audit, and certification. The benefits of implementing ISO 27001 are also significant and incorporate data protection, increased customer trust, and better risk management.
ISO 27001 certification is a strategic step for companies that want to ensure the highest level of information security and gain a competitive advantage in the market. We are pleased that our Drupal agency has successfully passed the certification process and can now guarantee customers the highest standards of data protection.











